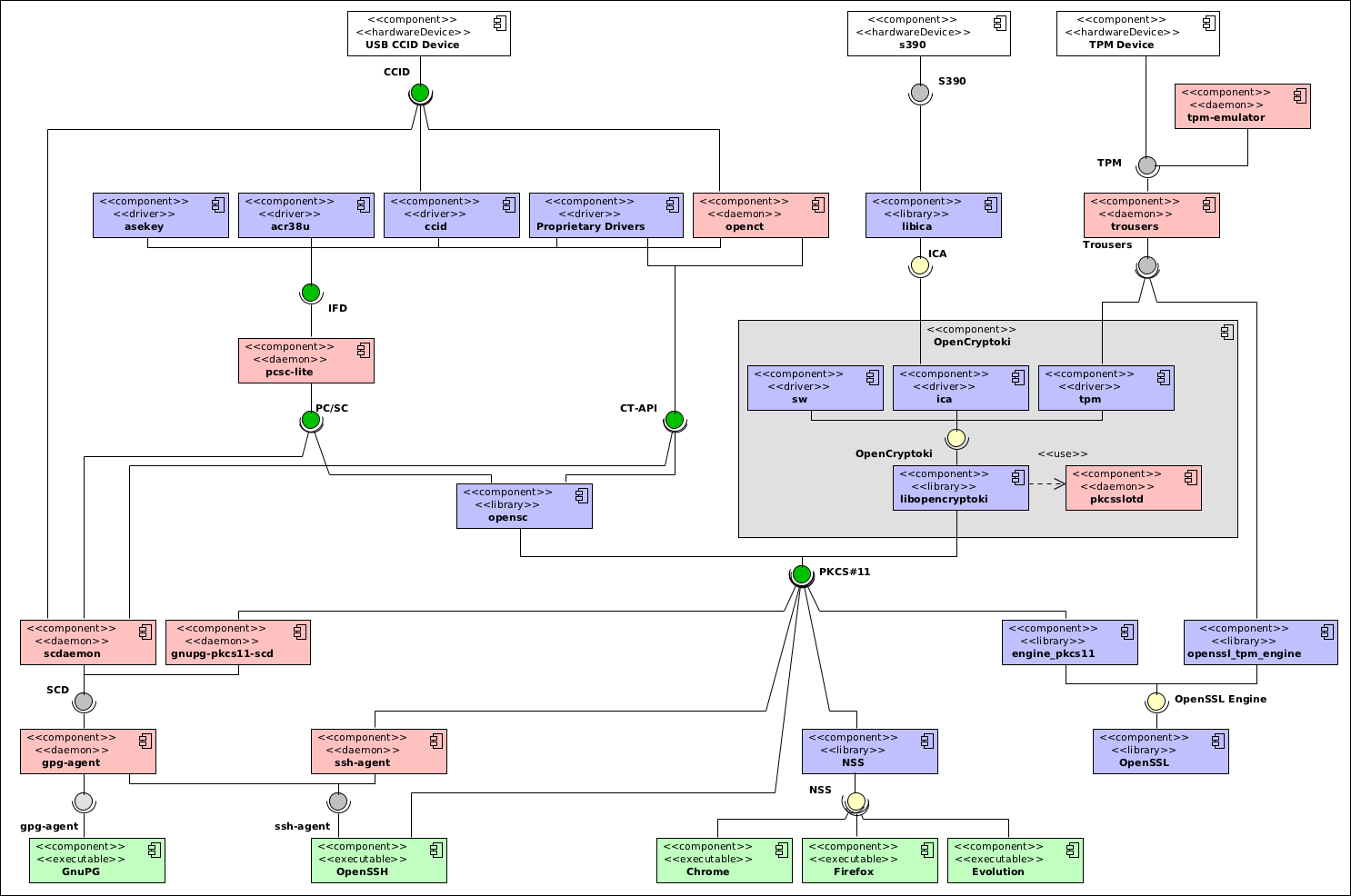
For EAP-TLS, you will need to read the cert from the PIV card to a local file. You can use the following command:
pkcs11-tool --module /usr/local/lib/opensc-pkcs11.so -r -y cert -d 01 -o cac-cert.der
wpa_supplicant.conf:
ctrl_interface=/var/run/wpa_supplicant
eapol_version=1
#ap_scan=1
#fast_reauth=0
pkcs11_engine_path=/usr/lib/ssl/engines/engine_pkcs11.so
pkcs11_module_path=/usr/local/lib/opensc-pkcs11.so
network={
ssid="test"
key_mgmt=WPA-EAP
eap=PEAP
proto=RSN
pairwise=CCMP
group=CCMP
identity="myname"
password="mschappass"
ca_cert="CA.pem"
phase1="peaplabel=0"
phase2="auth=MSCHAPV2"
priority=10
}
network={
ssid="test-tls"
key_mgmt=WPA-EAP
eap=TLS
proto=RSN
pairwise=CCMP
group=CCMP
identity="john@abctech.com"
ca_cert="CA.pem"
client_cert="cac-cert.der"
priority=10
engine=1
engine_id="pkcs11"
key_id="1:01"
pin="77777777"
}
#PEAP-EAP-TLS-SMARTCARD
#PEAP-EAP-TLS-SMARTCARD
network={
ssid="test-peap-eap-tls"
key_mgmt=WPA-EAP
eap=PEAP
proto=RSN
pairwise=CCMP
group=CCMP
anonymous_identity="noname@noname.com"
ca_cert="/etc/CA.pem"
identity="sean"
client_cert2="/tmp/cac-cert.der"
phase1="peapver=0"
phase2="auth=TLS"
priority=10
engine2=1
engine2_id="pkcs11"
key2_id="1:01"
pin2="77777777"
}
ssid="test-peap-eap-tls"
key_mgmt=WPA-EAP
eap=PEAP
proto=RSN
pairwise=CCMP
group=CCMP
anonymous_identity="noname@noname.com"
ca_cert="/etc/CA.pem"
identity="sean"
client_cert2="/tmp/cac-cert.der"
phase1="peapver=0"
phase2="auth=TLS"
priority=10
engine2=1
engine2_id="pkcs11"
key2_id="1:01"
pin2="77777777"
}
#key_id 1:01 means card reader at slot #1, and key id 01 on the card
To convert JTIC CA files to PEM format:
openssl pkcs7 -print_certs -in Certificates_PKCS7_v4.0.1_JITC.pem.p7b -out JITC-CA.pem
To Valid pin, have the card sign a simple file:
pkcs11-tool --sign -m SHA1-RSA-PKCS --input-file /etc/passwd --output-file /tmp/signature --pin 12345678
If signed successfully, then the pin is correct.
---Just for testing purpose---
To test your openssl engine
run: openssl, then
> engine -vvvv dynamic -pre SO_PATH:/usr/lib/ssl/engines/engine_pkcs11.so \
-pre ID:pkcs11 -pre LIST_ADD:1 -pre LOAD -pre VERBOSE \
-pre MODULE_PATH:/usr/local/lib/opensc-pkcs11.so
> req -engine pkcs11 -new -key 1:01 -keyform engine -x509 -out cert.pem -text
it will ask you for the PIN, and should generate a cert.pem if everything works.
------------Hostapd (including functioning as WiFi AP and RADIUS server)-----
hostapd.conf:
interface=wlan0
logger_syslog=-1
logger_syslog_level=2
logger_stdout=-1
logger_stdout_level=2
ctrl_interface=/var/run/hostapd
ctrl_interface_group=0
ssid=test-tls
hw_mode=g
channel=1
beacon_int=100
dtim_period=2
max_num_sta=255
rts_threshold=2347
fragm_threshold=2346
macaddr_acl=0
auth_algs=3
ignore_broadcast_ssid=0
wmm_enabled=1
wmm_ac_bk_cwmin=4
wmm_ac_bk_cwmax=10
wmm_ac_bk_aifs=7
wmm_ac_bk_txop_limit=0
wmm_ac_bk_acm=0
wmm_ac_be_aifs=3
wmm_ac_be_cwmin=4
wmm_ac_be_cwmax=10
wmm_ac_be_txop_limit=0
wmm_ac_be_acm=0
wmm_ac_vi_aifs=2
wmm_ac_vi_cwmin=3
wmm_ac_vi_cwmax=4
wmm_ac_vi_txop_limit=94
wmm_ac_vi_acm=0
wmm_ac_vo_aifs=2
wmm_ac_vo_cwmin=2
wmm_ac_vo_cwmax=3
wmm_ac_vo_txop_limit=47
wmm_ac_vo_acm=0
ieee8021x=1
eapol_key_index_workaround=0
eap_server=1
eap_user_file=hostapd.eap_user
ca_cert=./JITC-CA.pem
server_cert=./hostapd.server.pem
private_key=./hostapd.server.key
private_key_passwd=mypass
own_ip_addr=127.0.0.1
auth_server_addr=127.0.0.1
auth_server_port=1812
auth_server_shared_secret=radiussecret
radius_server_clients=./hostapd.radius_clients
radius_server_auth_port=1812
wpa=3
wpa_key_mgmt=WPA-EAP
wpa_pairwise=CCMP
rsn_pairwise=CCMP
hostapd.eap_user:
#john uses EAP-TLS and PEAP, everyone else uses PEAP and MSCHAPv2
"john@abctech.com" TLS
* PEAP
"john" MSCHAPV2 "mschappass" [2]
hostapd.radius_clients:
# RADIUS client configuration for the RADIUS server
127.0.0.1 radiussecret